myCSUSM
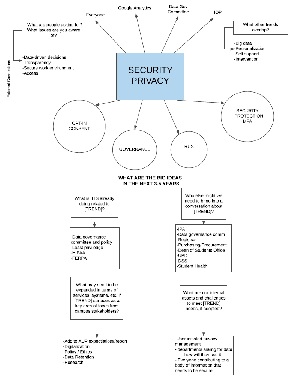
myCSUSMSecurity Privacy
CSUSM is committed to taking strong measures to protect the security and privacy of campus information assets, promoting the adoption of affordable learning materials, and deploying technologies that are equally accessible to all faculty, staff, and students. New policies from the CSU, as well as regulations from the state and federal governments, will require the campus to create new operational methods and purchase new technology solutions for compliance. Failure to do so may violate state or federal law, and will result in not only audit findings, but fines and costs associated with addressing or mitigating failures and breaches. These efforts will require both technology and personnel resources in order to adequately comply with the requirements.
Big Ideas (3-5 years)
- Opt-In Consent - means of express, affirmative, and explicit--for collecting sensitive data and for using personal data
- Governance - direct and control IT security - security strategies align with business objectives and consistent with regulations
- Trust
- Security - Multi-Factor authentication (MFA) - unique authentication code
Campus Connection
- Everyone - students, staff, faculty, administration
- Google Analytics - provide and protect the security of service
- Data Governance Committee
- Identity Management - designated users have the appropriate access to appropriate technology resources
What is IITS already doing related to Focus on Security Privacy?
- Data Governance Committee and campus policy to provide oversight and ensure data integrity
- Principle of Least Privilege (POLP) - limiting access to the minimal level that will allow normal functioning - lowest level of user rights that individuals can have and still do their jobs
- HIPAA - data privacy and security
- FERPA - privacy of student records and date in partnership with various custodians of record.
Who else might we need to bring into a conversation about Focus on Security Privacy?
- Institutional Planning & Analysis (IPA)
- Information Management Steering Committee and Data Governance Committee
- University Registrar
- Procurement and Contracts
- Dean of Students Office
- University Police
- Disabled Student Services
- Student Health and Counseling Services
What may need to be expanded in terms of services, systems, etc. if Focus on Security Privacy surfaces as a key area of focus from campus stakeholders?
- Acceptable Use Policy expectations/reports
- Digitalization - manage digital risk - Cybersecurity
- Policy / Ethics - established and enhance data security governance and flow
- Data Retention
- Research
What are our internal assets and challenges to meet Focus on Security Privacy needs, if adopted?
- User initiated privacy management - letting users understand the privacy
- Departments asking for data - Ad Hoc Data Request Form - how departments will use data - data released in accordance with FERPA and applicable CSUSM Policies - requests reviewed for appropriate use.
- Everyone contributing to a body of information that needs to be secure
What are people asking for? What issues are IITS aware of?
- Data-driven decisions - integrated planning and resource allocation, data and assessments, student learning outcomes
- Transparency
- Secure work environment
- Access to data