myCSUSM
myCSUSMBest Practices for Accessing Protected Data from Home
Throughout the new millennium the Internet has becoming integrated with every aspect of our lives. In 2012 74.8% of all US households have Internet use at home. We use this marvel of technology for everything from catching up with old friends to making money, and it is important that we protect ourselves when venturing out in to this new frontier.
With the ease of accessing campus resources from the web it is almost a guarantee that members of the campus community will access protected data from their home computer(s). Each member of the campus community has a responsibility to ensure that they are taking the necessary precautions to protect themselves and the campus from a potential breach of this information.
Protecting Yourself at Home
To maintain a secure computing environment at home we recommend you take the following actions:
- Purchase, install, and keep updated an anti-virus program that includes:
- Anti-Phishing Protection – Ensures the integrity of websites you visit by verifying URLs.
- Key Logger Protection – Usually some type of keystroke scrambler to prevent passwords and other important information from being seen if you get infected with a key logger.
- Email Scanning – Scans incoming email and attachments for viruses.
- Download Protection – Scans downloaded files for potential malicious code.
- Spyware/Malware Scans – Viruses are not the only malicious software you can be infected with.
- Speed – Anti-virus with a “Quick Scan” option might be a good choice if you don’t plan on spending a lot of time on your computer.
- Privacy Policy – Be sure to read the Privacy Policy to ensure that the company is not giving away your personal information.
View a list of important antivirus characteristics.
- Updating your computers operating system and other important 3rd party apps such as:
- Java
- Silverlight
- Your web browser of choice, be it Google Chrome, Firefox, Internet Explorer, Safari or any others.
- Microsoft Office
- Etc.
It is also recommended that you change password to important log-in credentials on a regular set interval. This includes websites such as, banking websites, primary email and other sites which would allow a malicious entity access to your personal private data. This ensures that if an adversary somehow gets your password, they only have access for at most the interval between when you change your passwords.
CougarApps
CougarApps is a technology to provide access to software licensed by the campus that would otherwise be unavailable at home. CougarApps creates an encrypted connection to our campus network, so it is a safe and secure way to connect to campus resources. CougarApps should always be your primary method of accessing confidential data from off-campus. More information on CougarApps.
Single Sign-On
Single Sign-On (SSO) allows users to enter their credentials once for a given set of linked websites, and remain logged in to all of the linked sites. Example: I sign in to Zoom through my web browser, and then I can sign in to Box without having to enter my log in credentials a second time.
While this is a wonderful feature that saves us time and headaches, it’s not without its faults. If you sign in any one of the linked sites using SSO, you must fully close the browser to ensure that you have logged off of all SSO sites. For Google Chrome users this is especially relevant because newer versions of Chrome stay open in the background, and require users to close the browser from the task bar.
Some of the web applications that use Single Sign-On here at CSUSM are:
- CSYou
- Box
- Zoom
- Cougar Jobs
- Educause Site
- Canvas
Unprotected Wi-Fi
Unprotected Wi-Fi is one of the most dangerous things out there. You connect to a hotel or Starbucks Wi-Fi and assume that it is safe, but really it’s not. Over an unsecured or unprotected Wi-Fi network is it easy for an adversary to see all your web traffic because the data is not encrypted or protected in any way. The same goes for your home Wi-Fi. If I drive around the neighborhood and find that your Wi-Fi is not secured with a passphrase I can easily connect, and then trick your computer in to thinking that I am the router, thereby seeing any and all network traffic that is taking place on your network.
For an enlightening read go to PC World article to see a few of the things that attackers can view over unprotected Wi-Fi.
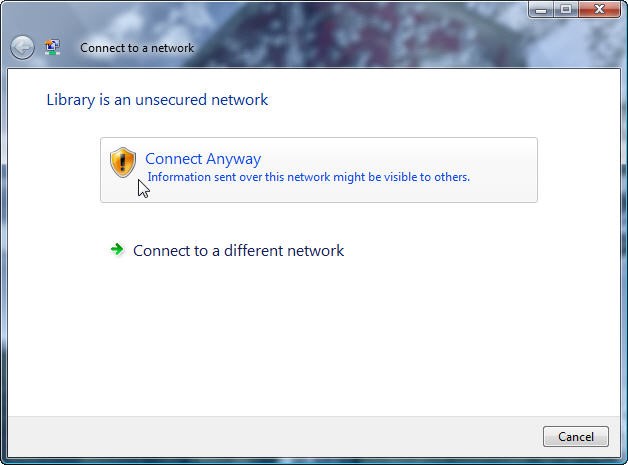 If you see a warning like the one shown above be very conscious of the things you
access while connected to this network.
If you see a warning like the one shown above be very conscious of the things you
access while connected to this network.
If you must conduct business using an unprotected Wi-Fi the following are some best practices:
- Every time you log in to a website, make sure that your connection is encrypted. The URL address should start with https instead of http.
- You also need to make sure that the connection stays encrypted for all of your online session. Some websites, including Facebook, will encrypt your log-in and then return you to an unsecured session—leaving you vulnerable.
- Many sites give you the option of encrypting your entire session. You can do this with Facebook by enabling Secure Browsing in the Security settings.
- When you check your email, try to login via the Web browser and ensure that your connection is encrypted (again, look for https at the beginning of the URL). If you use an email client such as Outlook, make sure your POP3 or IMAP and SMTP accounts are configured with encryption turned on.
- Never use FTP or other services that aren’t encrypted.
- To encrypt your Web browsing and all other online activity, use a VPN, or virtual private network (this article will show you how).
- Keep in mind that private networks have similar vulnerabilities: Anyone nearby can eavesdrop on the network. Enabling WPA or WPA2 security will encrypt the Wi-Fi traffic, obscuring the actual communications, but anyone who also has that password will be able to snoop on the packets traveling over the network.
The above list was created in part from information listed on PC World.
Using Wi-Fi at Home
We strongly recommend that if you’re using Wi-Fi at home you take these precautions:
- Secure your connection with a strong passphrase using letters and numbers. The passphrase should not be a dictionary word.
- Change the default username and password for your router.
- You should always change the default username and password credentials used to log in to your router.
- The default log in credentials are found quite easily with a quick Google search, and therefore are extremely insecure.
For most NETGEAR Devices
(except ReadyNAS/ReadyDATA products and FUlly Managed Switches), the default username and password are:
- Username (all models) = admin
- Password (current models) = password
- Password (very old models) = 1234
For ReadyNAS/ReadyDATA products
- Username (all models) = admin
- Password (latest models) = password
- Password (older models/firmwares) = netgear1
- Password (very old models) = infrant1
For NETGEAR Fully Managed Switches:
- Username (all models) = admin
- Password is blank (no need to enter any password)
Learn more at: Default web interface password for netgear devices
If you're looking for a new anti-virus you can check out this website for their "Top Ten Things to Look for in an Anti-Virus Program."